
5 Proven Ways to Mitigate the Cost of a Data Breach
| February 15, 2023No organization wants to suffer a data breach. But unfortunately, in today’s environment, it’s difficult to completely avoid them. Concensus Technologies assists with over a dozen security incidents every year. Approximately 83% of organizations have experienced more than one data breach. (IBM Security 2022 Cost of a Data Breach Report)
Read more: 5 Proven Ways to Mitigate the Cost of a Data BreachThese breaches hurt in many ways. First, there is the immediate cost of remediating the breach. Then, there are the lost productivity costs. An organization could also have extensive legal costs associated with a breach. To learn more about what a security incident vs. security breach read our blog post Data Breach vs. Security Incident.
According to IBM Security’s report, the cost of a data breach climbed again in 2022. The global cost of one breach is now $4.35 million, up 2.6% from last year. If your business is in the U.S., the cost rises to $9.44 million. In Canada, the average data breach costs companies $5.64 million.
Costs for smaller companies tend to be a little lower. But breaches are often more devastating to SMBs. They don’t have the same resources that larger companies do to offset all those costs.
It’s estimated that 60% of small companies go out of business within six months of a cybersecurity breach.
Organizations don’t need to resign themselves to the impending doom of a data breach. There are some proven tactics they can take to mitigate the costs. These cybersecurity practices can limit the damage of a cyberattack.
All these findings come from the IBM Security report. They include hard facts on the benefits of bolstering your cybersecurity strategy. Additionally, we have added our People, Process and Technology method to their findings.
Cybersecurity Tactics to Reduce the Impact of a Breach
Determine what you are trying to protect and find out where the data is first.
Most organizations do not realize the risk that is out there with their data as they do not have the right tools and processes in place to locate and minimize data loss. Leaving data with PII around on servers, laptops and mobile devices (Unstructured data) is a gold mine for threat actors.
At Concensus we utilize data loss protection techniques within Office 365 to mitigate possible data loss. We also work with all size organizations to discover, protect, and secure sensitive and high-value data. We can help you conduct a file analysis (on-premises and cloud) to quickly find sensitive data and secure it.
Use a Hybrid Cloud Approach
Most organizations use the cloud for data storage and business processes. Researchers found that 45% of all data breaches happen in the cloud. But all cloud strategies are not created equally.
Breaches in the public cloud cost significantly more than those in a hybrid cloud. What is a hybrid cloud? It means that some data and processes are in a public cloud, and some are in a private cloud environment.
What some may find surprising is that using a hybrid cloud approach was also better than a private cloud.
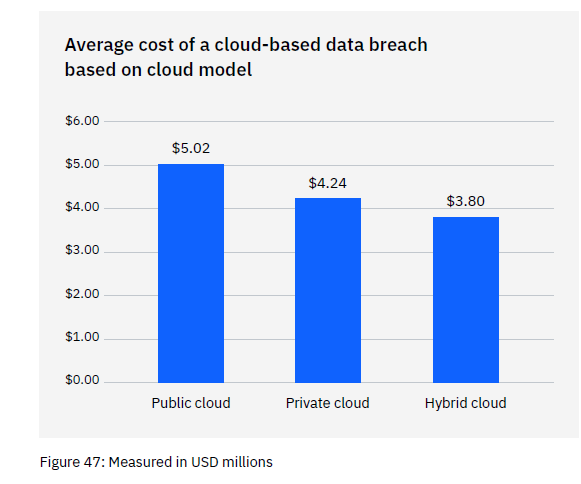
Graph from: IBM Security/Ponemon Institute 2022 Cost of a Data Breach Report
Create an Incident Response Plan & Practice It
You don’t need to be a large organization to create an incident response plan. This is a set of instructions and steps to take for employees to follow should any number of cybersecurity incidents occur.
Here is an example. In the case of ransomware, the first step should be disconnecting the infected device but do not power off the system. If forensics need to be completed on the system what is currently in Memory will help your response team with quicker resolution. Incident Response plans improve the speed and effectiveness of a response in the face of a security crisis.
Do not forget when developing this plan that individuals cannot work 24 hours a day 7 days a week. After 20 hours or so their effectiveness drops considerably. Add in the added stress of the incident and their effectiveness drops even earlier. The plan must include a team and not rely on just one person.
Implement a Zero Trust Security Approach
Zero trust is a collection of security protocols that work together to fortify a network. An example of a few of these are:
- Multi-factor authentication
- Application safelisting
- Contextual user authentication (Access Management)
Combining the tenants of zero trust and Identity and Access Management you can ensure that the right people have the right level of access to the right resources in the right context that is assessed continuously with the least friction possible.
Approximately 79% of critical infrastructure organizations haven’t adopted zero trust. Doing so can significantly reduce data breach costs. Organizations that don’t deploy zero trust tactics pay about $1 million more per data breach.
Use Tools with Security AI & Automation
Using the right security tools can make a big difference in the cost incurred during a data breach. Using tools that deploy security AI and automation brought the biggest cost savings.
Data breach expense lowered by 65.2% thanks to security AI and automation solutions. These types of solutions include tools like advanced threat protection (ATP). They can also include applications that hunt out threats and automate the response.
Concensus recommends a multi-layered approach to cybersecurity and using products that provide email security, contextual multi-factored authentication, endpoint detection and response need to be combined with a monitoring service.
Want to Improve Your Security & Reduce Risk in your Organization?
Don’t wait for a data breach or security incident to happen, take action now and secure your organization’s sensitive information. Contact Concensus online or by calling 724-898-1888 to schedule a security assessment.

