The Concensus Cyber Assistance Program (CAP) is a co-managed cybersecurity program designed to help the education community be more resilient to cybersecurity threats and provide the people, processes, and technologies to do so.
This cybersecurity program is the combination of core cybersecurity components plus identity and access management solutions with our Concensus Care Primary Engineers.
“Strategy without tactics is the slowest route to victory”. “Tactics without strategy is the noise before defeat” are two popular quotes from Sun Tzu’s art of war and they are very true with cybersecurity and IAM programs.
“Our strategy is to protect your end users from cyber threats by deploying a zero-trust model that focuses on users. Our tactics are to use the right people, the right processes, and right technologies to do so.” – Don DaRe President and CEO of Concensus Technologies
Zero Trust is a term for an evolving set of cybersecurity paradigms that move defenses from static, network based tactics to focus on users, assets and resources. At the core, zero trust does not assign trust based upon their physical or network location. Zero trust principles require the strict verification of users and devices before granting access to data or systems.
It is an important security consideration for IT administrators in schools as it can help protect sensitive data, such as student records and financial information.
The tenets of zero trust principles apply to all schools and universities and provide the perfect strategy for balancing security and ease of use in the classroom.
Our process from sales to co-management is depicted in the following diagram.
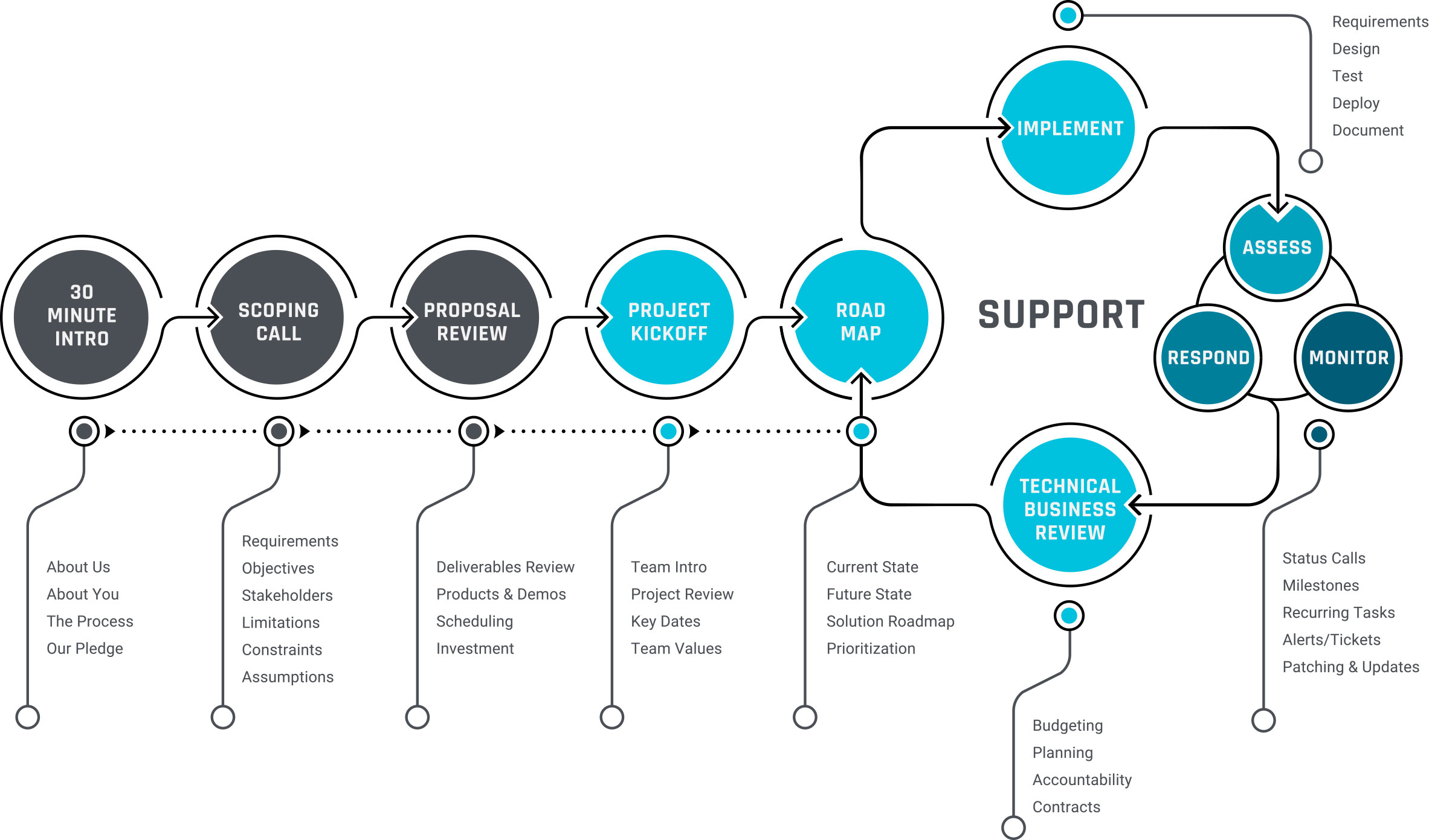
The assessment is designed to review your current state. We review all components of your cybersecurity program and IAM systems/programs. We also include a review of current needs and requirements such as compliance. Once a strategy is defined, we can then move forward with Future State Design.
The roadmap will create a phased and prioritized roadmap defining the set of activities required to implement your future state. This roadmap will explain all facets of the cybersecurity program, from first steps to long-term tactics to ensure ongoing security against evolving threats.
Concensus provides implementation services as part of a co-managed cybersecurity program. We always assign a Customer Success Manager with each engineer to ensure that projects are managed, broken into manageable phases and completed on time. We provide weekly and/or bi-weekly updates via planned status calls that track tasks, assignments, and issues. Stakeholders must be kept up to date with regular check-ins.
An important part of all our implementations is knowledge transfer. We want to ensure that our customers are up to date and knowledgeable about the solutions we implement. A cybersecurity program is useless if your people don’t understand how it works, so we prioritize giving you all the information you’ll need to make the most of our system.
Another benefit of the co-management is that your technical resource (Primary Engineer) does not leave for another project at the end of your project. The same engineer that provided the subject matter expertise becomes your primary contact and support engineer. They are a part of your team along with the Customer Success Manager. Some customers enter into this part of our process due to our engineer’s expertise within a discipline or software knowledge. We start supporting our customers as soon as we are contracted.
This phase is also when we are doing the Monitoring, Support, Patching and Responding to our customers’ needs in Cybersecurity and IAM.
The Technical Business Review (TBR) is a quarterly scheduled meeting with stakeholders and sponsors. The purpose of this meeting is to review the prior period, plan for the upcoming period and set milestones. At least once a year the contract is reviewed, and budgeting is discussed.
Many are familiar with the NIST framework for Identify, Protect, Detect, Respond, & Recover. The CAP program utilizes this foundation for identifying your strengths and gaps in your security. Many education organizations also face insurance and compliance requirements. The CAP cybersecurity program is designed to help with the following areas in cybersecurity:
Zero Trust and Identity and Access Management (IAM) complement each other in a comprehensive cybersecurity strategy.
Zero Trust is a security model that assumes that every user and device is a potential security risk, and it requires verifying the identity and ensuring the security of all entities before granting access to resources. A Zero Trust network requires identification and credentials every time, preventing incidents before they arise.
IAM, on the other hand, is the process of managing and controlling access to resources based on the identity of the user or device. It involves the secure management of digital identities and the authorization of access to resources based on predefined policies.
When Zero Trust and IAM are combined, they provide a multi-layered approach to securing access to resources. The Zero Trust model ensures that access is only granted after a thorough verification of identity, while IAM provides a system for managing and controlling access based on identity. This combination helps to prevent unauthorized access and ensures that only those who are authorized can access sensitive resources. Zero Trust networks are inherently much safer in design than most other security frameworks, with IAM principles further reinforcing this added security.
We offer solutions in the following areas:
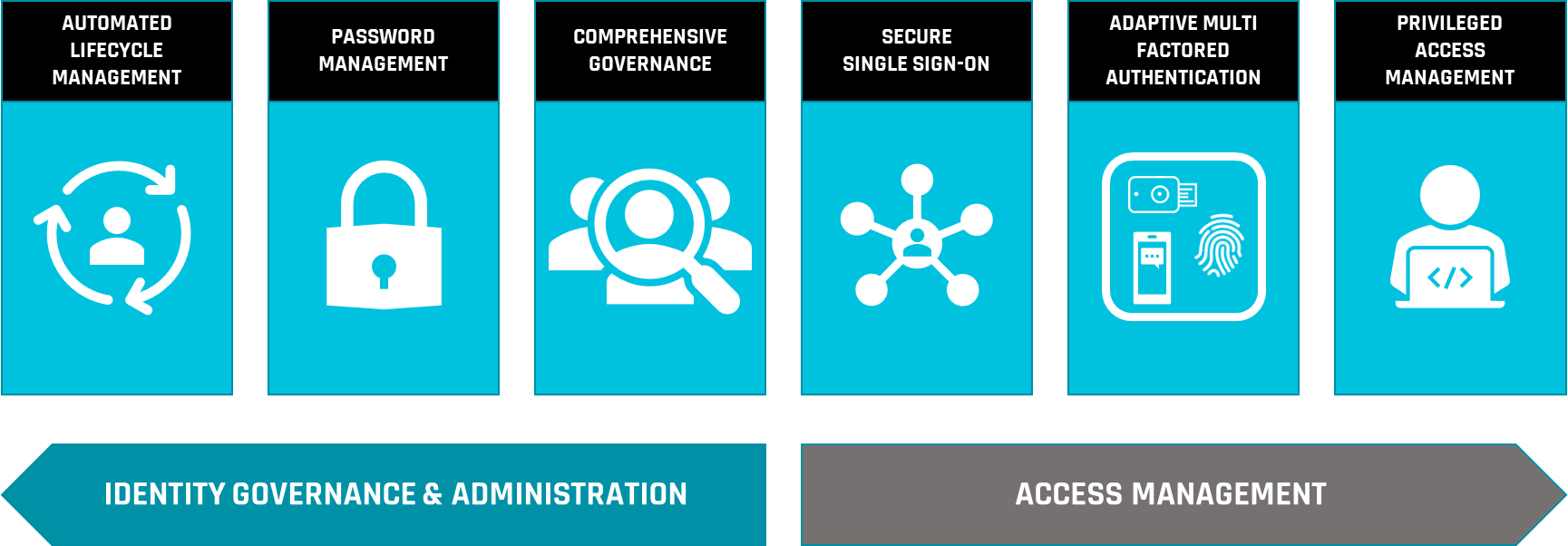
Combining the tenets of zero trust principles and IAM we can ensure that the right people have the right level of access, to the right resources, in the right context, which is assessed continuously with the least friction possible.
The last component is having the right people in the right seat. Our engineers are accountable and transparent, work together as a team and are humbly confident. They are continuously trained in areas of cybersecurity, IAM and business skills, with expertise in Zero Trust networks.
We offer dedicated and fractional engineers to help augment your staff and co-manage your IAM and cybersecurity programs.
For our education customers, we believe that co-management is an excellent balance of technical skills and budget. IT is only growing in complexity and scope. A co-managed, Zero Trust model allows the organization to fill in the gaps where there is a need.
Schools can benefit from this model by gaining access to experience and expertise that is not available internally.
Cybersecurity and IAM are two critical areas where there’s a skills gap in most schools. By using the co-managed model, you can gain access to critical resources and state of the art technology that will help you keep your infrastructure and critical date safe.