Every type of electronic device that connects to your network carries a massive security risk. Whether cell phones, computers, laptops, tablets, or others, these devices may carry viruses or additional risks that are or can be detrimental to your network security.
These devices may be corporate-owned, part of Bring_Your_Own_Device (BYOD) to work, or they may be accessing your network from an outside source. Modern Workplace Management can provide methodology and protection from these security risks, regardless of the device or the circumstances.
Modern Workplace Management covers all mobile, standard, and workplace devices, also known as Endpoints, and typically covers three main categories:
- Policies – Rules and regulations that govern the use of Endpoints
- Tools – Modern technologies and systems needed for early detection and overall security
- Procedures – Implementation and maintenance of Modern Workplace Management
Each of these categories contains a plethora of considerations unique to an organization and its users. Regardless of the size of your business, you need reliable Endpoint and Modern Workplace Management to ensure security and prevent or stop attacks. Since most companies are subject to some form of compliance and privacy regulations, protection for Endpoints is critical to help avoid hefty fines and damage to your reputation in the case of a security breach.
There are several key considerations and “must-haves” necessary for an effective and comprehensive Modern Workplace Management plan.
Policies
You will need to determine a series of workplace policies for the regulation of Endpoint devices. No matter what you decide the policy to be, you must make sure it is clearly stated and documented in your Employee Handbook and Acceptable Use Policy.
Many of the policies your organization needs to consider will concern rules governing using personal devices at work, also known as Bring_Your_Own_Device, or BYOD. Examples of these considerations include:
- Do you allow personal devices on your network? If not, be sure and clearly state this in your Employee Handbook and Acceptable Use Policy.
- What are the restrictions and acceptable use of personal devices? Many organizations will only support basic email, contact, and calendar functions on mobile devices.
- Do you allow personal devices for non-business use? If so, be sure to set up a guest wireless network and document the policy.
- Does your policy allow personal devices for business use? You should consider:
- The proper use of personal cell phones for business purposes
- Implications of hands-free, phone calls, and texting functions while driving
- State laws on personal cell phone use and general liability, especially when distracted by business calls or texts while driving
Tools
The second main category of Modern Workplace Management is the tools and technologies you are going to implement to enforce your policies and ensure the overall security protection of your network. Here are a few recommendations.
- Upgrading to Microsoft Windows 10 – In early 2020, Microsoft will no longer support older versions of Windows. While older versions will continue to function, the available support for backup, security, office applications, and other business applications will no longer exist. Older machines should be upgraded to Windows 10 or replaced. When upgrading, be sure that you are using the Professional or Enterprise version.
- Device Patching and Upgrading – Currently, security depends on constant updates to the operating system and your applications. Requiring Remote Monitoring and Management tools enables IT to manage and support electronic devices in a central location.
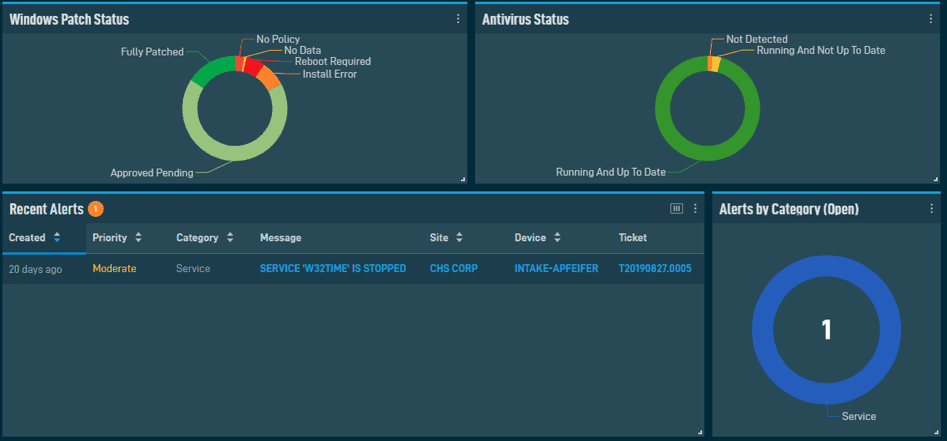
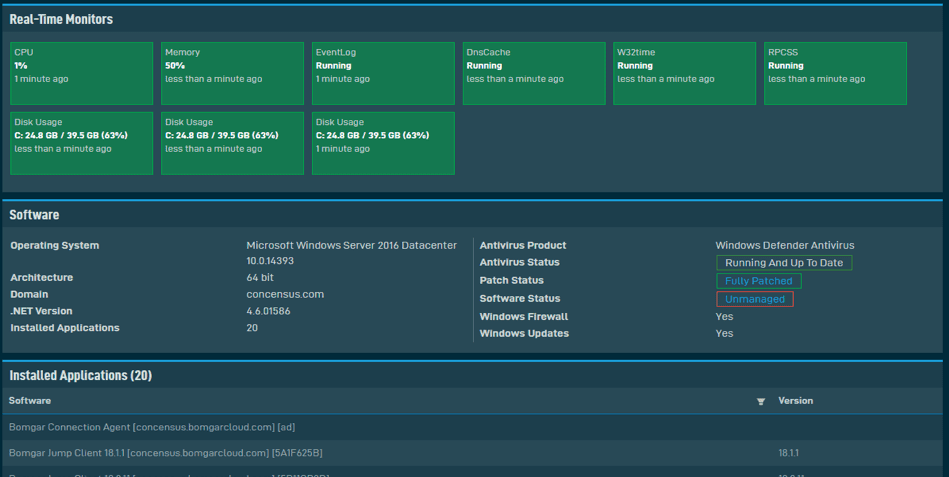
- Endpoint Detection and Response – In addition to anti-virus or personal firewalls, tools must include advanced threat detection known as EDR (Endpoint Detection and Response) for enabling faster response times. For instance, when an Endpoint encounters a never-before-seen threat, the EDR monitors the new threat, categorizes it as malicious, and allows for an immediate response.
- Device Backup – If a laptop is compromised, you could experience a complete data loss or fall victim to a malware attack. Fortunately, software is available to back up files and even image the entire device. Just like backing up a server, you’ll be able to recover from data loss quickly.
- Device Encryption – This is a mandate for laptops in case of theft, especially those that contain Personal Identification Information (PII).
- For Windows-based laptops, we recommend using Bitlocker to encrypt your devices’ internal disk drives, which prevents someone from accessing the data on your device.
- Mac users can also utilize FileVault feature built into the operating system.
Procedures for Implementation
The third main category of Modern Workplace Management is developing a methodology that aligns with the organizational goals, as well as budgetary allowances and constraints.
At Concensus, our methodology is part of our Concensus Care program. Our process is as follows:
- Current Environment Review – Existing environments must be thoroughly reviewed from a bottom-to-top approach. That starts with the cabling through the required applications. The review may include a network scan or even deployment of a remote monitoring and management software that can gather all the necessary data to put together a technology roadmap.
- Technology Roadmap – This is prioritizing and organizing projects and items based on budget, security, and need.
- Implementation Projects – Projects go beyond day-to-day operations. Each project will have unique goals to implement and provide the latest security measures for your organization.
At Concensus, we’re your experts in Cybersecurity, and we’re also your experts in Modern Workplace Management, security, and solutions. Whether you have questions, need more information, or are ready to move forward, contact our sales team or visit our website to schedule your review at www.concensus.com/healthcheck.
Let us give you peace of mind
Leave it to our experts to keep your organization secure around the clock. Partner with us for trusted technology support.
