Zero Trust has been a buzzword in the Identity and Access world for quite some time, but it is still very much at the forefront of cyber security professionals’ minds. So, what exactly is Zero Trust and why is there such a strong push for identity professionals to make the move toward this approach?
Contrary to popular belief Zero Trust is not a product an organization can go out and purchase through any one vendor, instead Zero Trust is a policy approach. It has been accepted in the industry as a reliable security model to address concerns of the decentralized office.
What is Zero Trust, and Why Does it Matter?
As noted above, Zero Trust is a cyber security model that addresses the modern trend seen in a more mobile workforce that has been emerging over the past few years. When individuals move from the office to their home office, we can no longer strictly rely on the access controls of the physical building and the network-specific boundaries of the office. With the shift to a mobile workforce, agencies are forced to rethink security.
CISA (the US Cybersecurity and Infrastructure Security Agency) breaks out Zero Trust policy into five main pillars of focus: Identity, Device, Network, Application, and Data. Each one of these pillars helps to create an overarching security approach that leaves little room for risk. When approaching the task of creating a Zero Trust policy it is imperative to consider each of the pillars carefully. This approach aims to reduce the risk of unauthorized users gaining access to data and services through granular access controls.
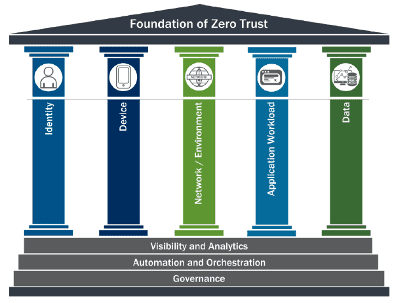
How to Protect the Pillars
Each pillar needs to be carefully considered and addressed in the policy to protect organizational assets. Below you will find considerations for Identity, Device, Network, Applications, and Data.
Zero trust with Identity
Much of the concerns with the mobile network can be addressed by looking at how individuals access the network and tools on a regular basis. The goal is to ensure that only the right users and entities have just the necessary levels of access to tools for daily tasks and only at the right times. Consider the below for Identity:
- Use of Multifactor authentication with users authenticate
- User login and behavior analytics/ reporting
- User risk level- is any one user or group to be targeted due to increased access?
- How often should users be reauthenticated?
- Federating Identity through on-prem, hybrid, and cloud environments
- Governance to continually reassess the level of access allowed to individuals and resources
Protecting the Device
The hardware used to access the network are no longer always a managed device and each can come with its own security concerns. When approaching how to best protect the organization from a device-based focal point consider the below.
- How are you monitoring device posture for managed and unmanaged devices? What level of visibility do you have?
- How often do you reassess devices for posture compliance?
- How are managed devices provisioned and are they kept up to date on security patches.
Ensuring the Network
Network at its core is agency internal networks, wireless networks, the Internet, and any network used to transport messages. As users move out of the office protection from firewalls and air gapping becomes more difficult. Restricting internet access is not as much of an option as before. Things to consider are:
- Network Segmentation
- Threat Detection processes
- Encryption of data/ communications in Transit
- Visibility and reporting around network access
Application Security Considerations
Applications with varying levels of access to sensitive data must be considered as well. One must ensure they are protecting business secrets and PII of employees/ customers.
- Who has access to what applications?
- How are we protecting applications with access to sensitive data?
- Is access to applications automatically provisioned/de-provisioned?
- Visibility and reporting around who has access to what applications.
Data Protection
Agency data needs to be protected whether it resides on devices, in applications, or across networks. It is also imperative to protect data at rest and in transit, as well as deployment of mechanisms for detection of data exfiltration. Things to consider with Data Protection:
- Who has access to sensitive data?
- What sort of encryption should be used? When?
- Data Access Governance and Certification
Closing
Government mandates and compliance requirements continue to push for stronger security every day. Ensure you are meeting these requirements by implementing a strong Zero Trust approach.
Let us give you peace of mind
Leave it to our experts to keep your organization secure around the clock. Partner with us for trusted technology support.
