
What is Stopping you from Changing IT Providers? – GETTING STARTED
| December 30, 2020In our first blog post, we discussed why change is hard and why you need to formalize your process so that you can compare IT providers. This second blog in the series will focus on where to start.
What is important?
The absolute first thing you need to decide is what is important to you and not to the IT department. We suggest that you look at your digital assets from both a security and business impact first. Why security? In today’s world, no matter what size organization you have, security must be at the center of your IT plan. If you have compliance such as HIPAA, PCI, FDIC, GLBA, FERPA, or even GDPR, you must take the necessary security precautions with your data. IT today centers around what digital assets are we trying to protect.
Here are examples of digital assets that need protecting:
- Personal Identifiable Information (PII) – Think home salary, address, SSN, driver’s license etc. If you keep that in your HR or accounting systems, it must be protected.
- Personal Health Information (PHI) – If you are in-health care this is HIPAA related.
- Customer and vendor lists – What happen if you lose access to these?
- Line of business applications – What if I can not access that one application that we run our business on?
- Passwords, lists, proposals, documents, etc.
If you’re not sure what is important, ask the person who runs that department. What can’t we lose? What happens if that system is gone? How long can we afford to be down?
Make a simple table:
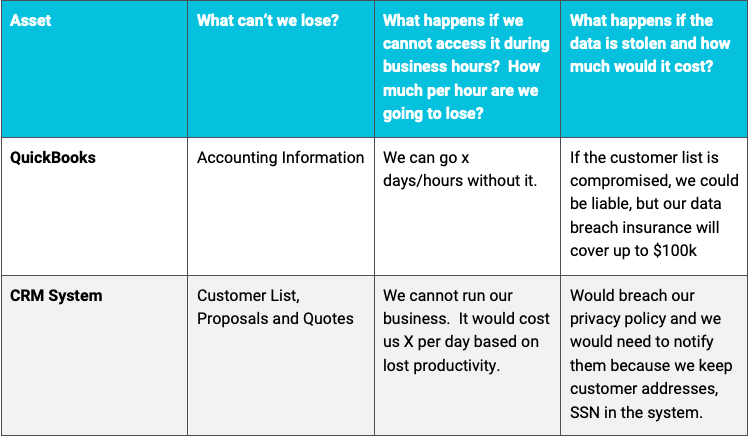
WHO needs Access to Your important data?
Today’s IT security best practices assumes zero-trust. That means no one is trusted with access to the data. It is more than a buzzword. It is a trust model with the assumption that no matter where people are accessing the data from, they must have the proper access. There are systems today that can detect an irregular login and deny access because of the high-risk factor. For example, you could restrict remote access to someone who 5 minutes ago logged in from Pittsburgh, Pennsylvania, and is trying to access a different resource from Austin, Texas. By understanding who needs access i.e. customers, employees, contractors, students, department, or a subset of any of those groups, you can help build out your layers of security.
If you made your list of important assets, add two more columns and name one “Who needs access” and the other “How do they access it?” Depending on the size of your business, you will simply answer people or groups of people (roles) for the first column. In the second column, write down things like “internal only,”” from home,” or “from anywhere,” based upon your requirements.
What Equipment do we have?
It is important to know the inventory of your systems. Servers, desktops, laptops, printers, firewalls, wireless access points, phones, etc. If you have this information in a spreadsheet or an asset inventory system, you will at some point need to hand that over to a potential provider. If you have a current provider, ask them to provide a report of your managed devices. Some providers will price their services based on users/servers, while others use a more traditional device count.
Summary
If you’ve made it this far through the blog, we’ve helped you organize by who and what you need to protect. You know how long you can afford to be down and what the consequences of being down are. This was all done without the need to involve IT. This is the start of a risk assessment. What is key here is that while we are talking about risk, we did not discuss the measurement of those risks (the measure of impact versus the likelihood that something bad will happen). At Concensus, we recommend a thorough approach to a risk assessment that focuses on asset owners and power users before engaging IT or reviewing each system.
TIP: Some providers will provide a network vulnerability scan that lists all applications and devices on the network. This is not a true measurement of a risk. These scans are an essential part of a cybersecurity program (and all good providers can do them) but they are not focused on the impact of those vulnerabilities. What they are usually used for by these providers is to show you that you haven’t patched something and that there are x number of devices on your network (that they in turn want paid to manage).
Concensus offers true risk assessments for your organization as well as a complete set of solutions for cybersecurity, cloud, and managed IT services for your business. Concensus provides complete cybersecurity, managed IT services, and IaM solutions for your business. Reach out to our team for a consultation.
This is the second in our blog series of, “What’s stopping you from changing IT Providers.” If you missed the first blog or would like to read on to our third blog, click below.

