
Explaining Cybersecurity Audits
| November 16, 2021Whether you are a small business or a large enterprise, you need more than the latest anti-virus to ensure that your company’s network is secure. A cybersecurity audit helps you create a complete picture of your security strategy.
Concensus Technologies has seen firsthand how cybercrime has grown into one of the epidemics of modern times.
In 2020 We saw a 600% cybercrime from the previous years. Estimates state that ransomware attacks will cost companies over $6 trillion in 2021.
If you do not prioritize cybersecurity, you are placing yourself and your company at risk of attack.
It is very likely that you already have some strategies to combat attacks and malicious cyber forces. However, it would help if you felt that your measures were layered and provided you with adequate business continuity.
That’s where cybersecurity audits become important.
In this article, Concensus Technologies cybersecurity experts will examine these audits and share some crucial tips for running one in your school or company.
What is a cybersecurity audit?
Think of an audit as a comprehensive examination of every cybersecurity system, software, and policy you have put in place. There will be several goals with a cybersecurity audit:
- Identify any gaps in your system.
- Create what is known as an in-depth report (this will help demonstrate that you have the proper strategies in place to defend against an attack.
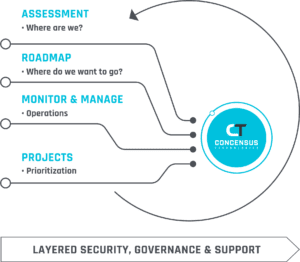
A typical audit contains three phases:
- Assessment (where are we?)
- Roadmap (Prioritize and Assignment)
- Audit
In the assessment phase, you are examining the existing system(s). At Concensus, this will include a review of your organization’s systems, software, and databases. We would also review how you assign rights to end-users and any software or hardware you are using to defend against cybersecurity threats. This will provide you with a list of gaps that need to be addressed during the roadmap phase.
During the roadmap phase, you will review all of the current gaps in your organization. Here you will need to assign the appropriate solutions to the issues identified. You will need to prioritize these in terms of need, speed, and ultimately cost. Note that you will either need to assign internal professionals these tasks, or you might need to bring in external subject matter experts to help with your implementation.
Finally, you will conclude with an audit that takes place after your solution(s) are put in place. This is intended to ensure that all installations, upgrades, patches, etc., operate as expected.
The three tips for a successful cybersecurity audit
Now that you understand the phases of a cybersecurity audit, you need to know how to run an audit effectively to provide the information you need. After all, a poorly conducted audit may miss crucial security gaps, leaving your systems vulnerable to attack.
The following tips will help you conduct a small/medium-sized cybersecurity audit in your organization.
TIP #1 – Check for the age of your existing security systems
Systems that are not patched or automatically updated do not protect you against evolving cyber threats.
Hackers continually change their tactics to create a breach.
This means you should check the age of your existing systems.
Make sure to update your systems whenever the manufacturer releases an update. If the manufacturer no longer supports the software or hardware you have, that is a sign that it’s time for an upgrade. Leaving a system in place that is no longer supported or updated leaves it vulnerable to threats.
TIP # 2 – IDENTIFY THE THREATS AND WHAT YOU NEED TO PROTECT
As you conduct your small/medium organizational cybersecurity audit, identify your most important assets to protect. For example, if you have a system containing customer/client/hr or student information, data privacy is crucial. In this situation, threats could arise from something like weak passwords, phishing attacks, or malware.
Threats can always come internally, possibly from malicious employees/students or through mistaken provisioning of access rights to individuals who shouldn’t be able to see specific data.
Allowing staff/students/employees/guests to connect their own devices to your network creates risk because you have no control over the security of those devices.
To summarize, review your most important assets and what threats you face before implementing any solutions.
TIP #3 – EDUCATE YOUR EMPLOYEES AND TEST THEM
After identifying your digital assets and reviewing the threats posed against them, you must focus on creating a cybersecurity program that includes training. Training them will ensure that your employees can safeguard against phishing and malware attacks. If you face an emergency, such as a data breach, and your employees do not know how to respond, you run the risk of further breaches and catastrophic data loss.
To avoid this situation, you should educate them on what to look out for and how to respond to these threats. A training plan must incorporate the following:
- The various threat types you’ve identified and how to look out for them.
- Where they can go to access additional information about a threat
- Who they should contact if there is a threat.
- How long it should take to rectify the danger.
- Any policies you have in place that include using external devices or accessing data stored on secure systems.
Consider investing in a training platform that includes Security Awareness Training and make that part of your HR team’s onboarding. Many cybersecurity insurance policies want to know the last time you ran a company-wide phishing test and the click rate.
By educating your employees about the threats and how to respond to them, you will create one more layer of defense against cybersecurity threats.
How Audits improve Security
Cybersecurity audits offer you a chance to improve your security posture. They can help you to identify issues and keep you up to date on the latest threats.
Remember that security solutions are not one and done.
It is essential to consider a multi-layered security model and continue reassessing your processes and systems – a minimum of once a year.
Concensus can help you with a full cybersecurity program for your organization. Our lifecycle program will help your organization secure your most important digital assets and continually keep you up to date. We offer a free high-level cybersecurity assessment for your organization to help you identify key areas. Sign up here!

